[ad_1]
Getty Photos
For those who’re utilizing Amazon Net Companies and your S3 storage bucket might be reached from the open net, you’d do nicely to not decide a generic title for that house. Keep away from “instance,” skip “change_me,” do not even go together with “foo” or “bar.” Another person with the identical “change this later” considering can price you a MacBook’s value of money.
Ask Maciej Pocwierz, who simply occurred to choose an S3 title that “one of many in style open-source instruments” used for its default backup configuration. After establishing the bucket for a shopper venture, he checked his billing web page and located practically 100 million unauthorized makes an attempt to create new recordsdata on his bucket (PUT requests) inside at some point. The invoice was over $1,300 and counting.
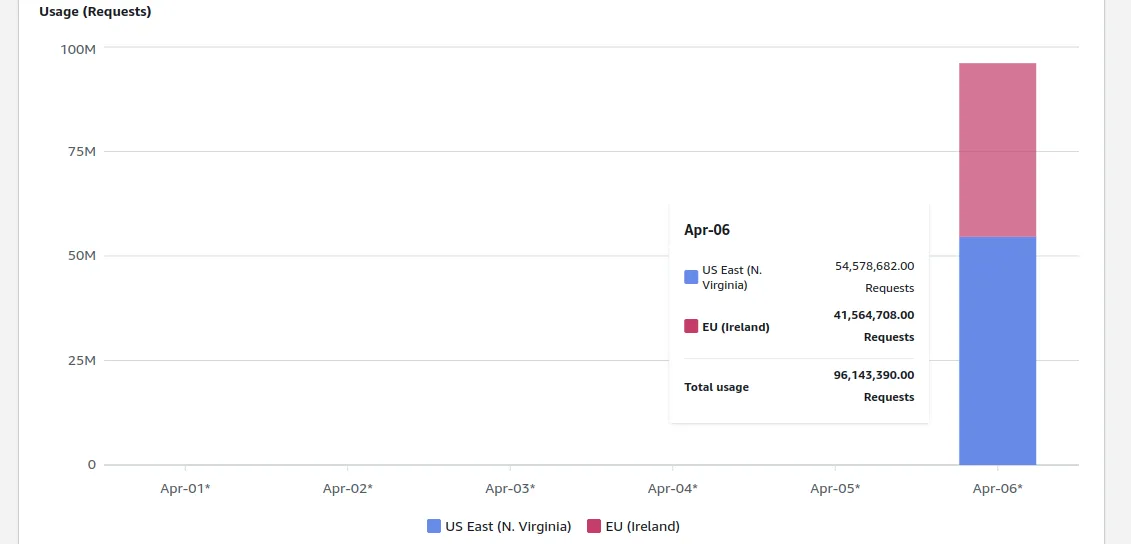
Nothing, nothing, nothing, nothing, nothing … practically 100 million unauthorized requests.
“All this really occurred just some days after I ensured my shopper that the worth for AWS providers might be negligible, like $20 at most for the whole month,” Pocwierz wrote over chat. “I defined the state of affairs may be very uncommon however it positively seemed as if I did not know what I am doing.”
Pocwierz declined to call the open supply software that inadvertently bum-rushed his S3 account. In a Medium post about the matter, he famous a special downside with an unfortunate default backup. After turning on public writes, he watched as he collected greater than 10GB of information in lower than 30 seconds. Different individuals’s knowledge, that’s, and so they had no concept that Pocwierz was amassing it.
A few of that knowledge got here from corporations with clients, which is a part of why Pocwierz is retaining the specifics below wraps. He wrote to Ars that he contacted a few of the corporations that both tried or efficiently backed up their knowledge to his bucket, and “they utterly ignored me.” “So now as a substitute of getting this fastened, their knowledge continues to be in danger,” Pocwierz writes. “My lesson is that if I ever run an organization, I’ll positively have a bug bounty program, and I’ll deal with such warnings significantly.”
As for Pocwierz’s accounts, each S3 and financial institution, it principally ended nicely. An AWS consultant reached out on LinkedIn and canceled his invoice, he mentioned, and was informed that anyone can request refunds for extreme unauthorized requests. “However they did not explicitly say that they may essentially approve it,” he wrote. He famous in his Medium publish that AWS “emphasised that this was finished as an exception.”
In response to Pocwierz’s story, Jeff Barr, chief evangelist for AWS at Amazon, tweeted that “We agree that clients shouldn’t should pay for unauthorized requests that they didn’t provoke.” Barr added that Amazon would have extra to share on how the corporate may stop them “shortly.” AWS has a quick explainer and speak to web page on unexpected AWS charges.
The open supply software did change its default configuration after Pocwierz contacted them. Pocwierz steered to AWS that it ought to limit anybody else from making a bucket title like his, however he had but to listen to again about it. He suggests in his weblog publish that, past random dangerous luck, including a random suffix to your bucket title and explicitly specifying your AWS area might help keep away from large prices just like the one he narrowly dodged.
[ad_2]
Source link








