[ad_1]
The FBI spent a lot of Tuesday locked in an internet tug-of-war with one of many Web’s most aggressive ransomware teams after taking management of infrastructure the group has used to generate greater than $300 million in illicit funds so far.
Early Tuesday morning, the dark-web website belonging to AlphV, a ransomware group that additionally goes by the identify BlackCat, abruptly began displaying a banner that mentioned it had been seized by the FBI as a part of a coordinated regulation enforcement motion. Gone was all of the content material AlphV had posted to the positioning beforehand.
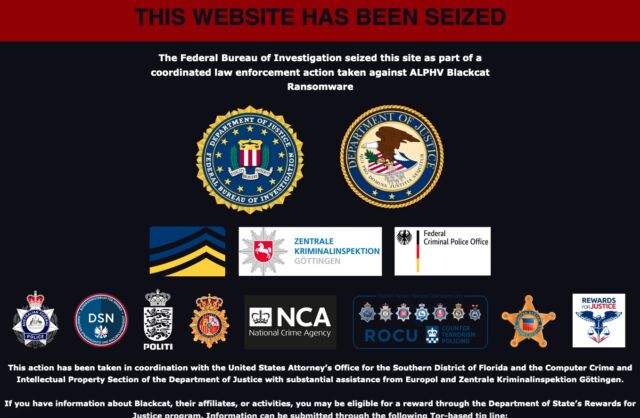
Across the similar time, the Justice Division said it had disrupted AlphV’s operations by releasing a software program software that may enable roughly 500 AlphV victims to revive their methods and information. In all, Justice Division officers mentioned, AlphV had extorted roughly $300 million from 1,000 victims.
An affidavit unsealed in a Florida federal court docket, in the meantime, revealed that the disruption concerned FBI brokers acquiring 946 personal keys used to host sufferer communication websites. The authorized doc mentioned the keys have been obtained with the assistance of a confidential human supply who had “responded to an commercial posted to a publicly accessible on-line discussion board soliciting candidates for Blackcat affiliate positions.”
“In disrupting the BlackCat ransomware group, the Justice Division has as soon as once more hacked the hackers,” Deputy Legal professional Common Lisa O. Monaco mentioned in Tuesday’s announcement. “With a decryption software offered by the FBI to a whole lot of ransomware victims worldwide, companies and faculties have been capable of reopen, and well being care and emergency companies have been capable of come again on-line. We are going to proceed to prioritize disruptions and place victims on the middle of our technique to dismantle the ecosystem fueling cybercrime.”
Inside hours, the FBI seizure discover displayed on the AlphV dark-web website was gone. Instead was a brand new discover proclaiming: “This web site has been unseized.” The brand new discover, written by AlphV officers, downplayed the importance of the FBI’s motion. Whereas not disputing the decryptor software labored for 400 victims, AlphV officers mentioned that the disruption would forestall information belonging to a different 3,000 victims from being decrypted.
“Now due to them, greater than 3,000 corporations won’t ever obtain their keys.”
Because the hours went on, the FBI and AlphV sparred over management of the dark-web website, with every changing the notices of the opposite.
One researcher described the continuing battle as a “tug of Tor,” a reference to Tor, the community of servers that enables folks to anonymously browse and publish web sites. Like most ransomware teams, AlphV hosts its websites over Tor. Not solely does this association forestall regulation enforcement investigators from figuring out group members, it additionally hampers investigators from acquiring court docket orders compelling the online host to show over management of the positioning.
The one approach to management a Tor deal with is with possession of a devoted personal encryption key. As soon as the FBI obtained it, investigators have been capable of publish Tuesday’s seizure discover to it. Since AlphV additionally maintained possession of the important thing, group members have been equally free to publish their very own content material. Since Tor makes it inconceivable to vary the personal key equivalent to an deal with, neither aspect has been capable of lock the opposite out.
With all sides basically deadlocked, AlphV has resorted to eradicating among the restrictions it beforehand positioned on associates. Underneath the widespread ransomware-as-a-service mannequin, associates are those who truly hack victims. When profitable, the associates use the AlphV ransomware and infrastructure to encrypt information after which negotiate and facilitate a cost by Bitcoin or one other cryptocurrency.
To this point, AlphV positioned guidelines on associates forbidding them from concentrating on hospitals and significant infrastructure. Now, these guidelines not apply until the sufferer is situated within the Commonwealth of Impartial States—a listing of nations that have been as soon as a part of the previous Soviet Union.
“Due to their actions, we’re introducing new guidelines, or somewhat, we’re eradicating ALL guidelines besides one, you can’t contact the CIS, now you can block hospitals, nuclear energy crops, something, anyplace,” the AlphV discover mentioned. The discover mentioned that AlphV was additionally permitting associates to retain 90 p.c of any ransom funds they get, and that ‘VIP’ associates would obtain a non-public program on separate remoted information facilities. The transfer is probably going an try and stanch the doable defection by associates spooked by the FBI’s entry to the AlphV infrastructure.
The backwards and forwards has prompted some to say that the disruption failed, since AlphV retains management of its website and continues to own the info it stole from victims. In a dialogue on social media with one such critic, ransomware professional Allan Liska pushed again.
“The server and all of its information continues to be in possession of FBI—and ALPHV ain’t getting none of that again,” Liska, a menace researcher at safety agency Recorded Future, wrote.
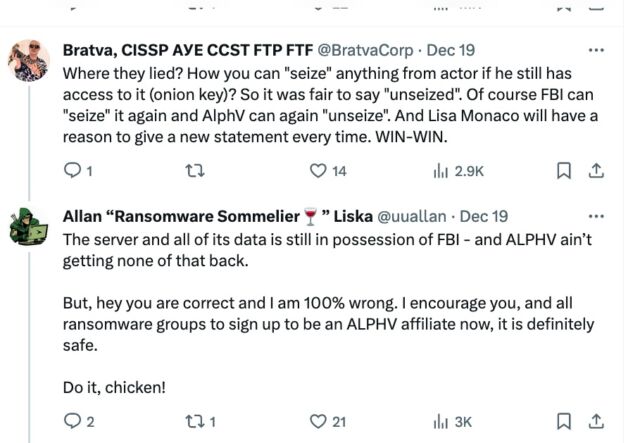
“However, hey you might be appropriate and I’m 100% incorrect. I encourage you, and all ransomware teams to enroll to be an ALPHV affiliate now, it’s positively protected. Do it, Rooster!”
[ad_2]
Source link








