[ad_1]
Aurich Lawson | Getty Photographs
Up to now 12 months, a brand new time period has arisen to explain a web based rip-off raking in millions, if not billions, of {dollars} per 12 months. It’s known as “pig butchering,” and now even Apple is getting fooled into collaborating.
Researchers from safety agency Sophos said on Wednesday that they uncovered two apps accessible within the App Retailer that have been a part of an elaborate community of instruments used to dupe individuals into placing giant sums of cash into faux funding scams. At the very least a kind of apps additionally made it into Google Play, however that market is infamous for the variety of malicious apps that bypass Google vetting. Sophos mentioned this was the primary it had seen such apps within the App Retailer and {that a} previous app recognized in these kind of scams was a professional one which was later exploited by dangerous actors
Pig butchering depends on a wealthy mixture of apps, web sites, net hosts, and people—in some circumstances human trafficking victims—to construct belief with a mark over a interval of weeks or months, usually beneath the guise of a romantic curiosity, monetary advisor, or profitable investor. Ultimately, the web dialogue will flip to investments, normally involving cryptocurrency, that the scammer claims to have earned large sums of cash from. The scammer then invitations the sufferer to take part.
As soon as a mark deposits cash, the scammers will initially enable them to make withdrawals. The scammers finally lock the account and declare they want a deposit of as a lot as 20 p.c of their stability to get it again. Even when the deposit is paid, the cash isn’t returned, and the scammers invent new causes the sufferer ought to ship extra money. The pig-butchering time period derives from a farmer fattening up a hog months earlier than it’s butchered.
Abusing belief within the App Retailer
Sophos mentioned that it not too long ago discovered two iOS listings within the App Retailer that have been used for CryptoRom, a kind of pig butchering that makes use of romantic overtures to construct the boldness of its victims. The primary was known as Ace Professional and claimed to be an app for scanning QR codes.
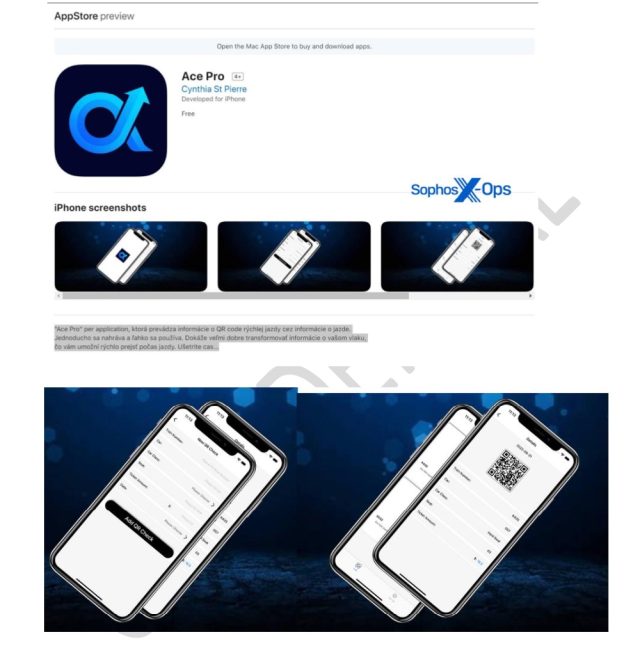
The second app was MBM_BitScan, which billed itself as a real-time knowledge tracker for cryptocurrencies. One sufferer Sophos tracked dumped about $4,000 into the app earlier than realizing it was faux.

Apple is known for its repute—warranted or in any other case—for filtering out malicious apps earlier than they find yourself within the App Retailer. Mixed with detailed faux on-line profiles and elaborate backstories the scammers use to lure victims, the presence of the apps within the App Retailer made the ruse all of the extra convincing.
“If criminals can get previous these checks, they’ve the potential to achieve hundreds of thousands of gadgets,” Sophos researchers wrote. “That is what makes it extra harmful for CryptoRom victims, as most of these targets usually tend to belief the supply if it comes from the official Apple App Retailer.”
Apple representatives didn’t reply to an electronic mail requesting an interview for this story. Google PR additionally declined an interview however mentioned in an electronic mail the corporate eliminated the app after receiving a heads-up from Sophos.
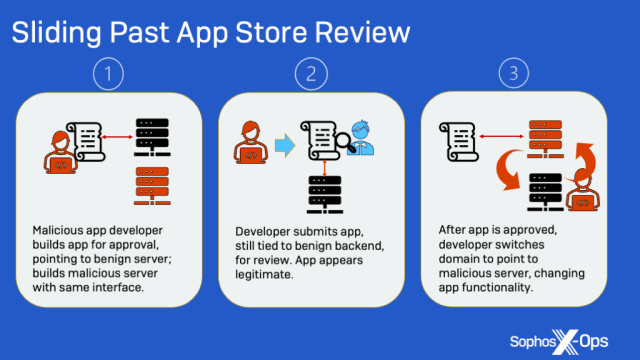
Ace Professional and MBM_BitScan circumvented Apple’s vetting course of through the use of distant content material downloaded from hardcoded net addresses to ship their malicious performance. When Apple was reviewing the apps, the websites probably delivered benign content material. Ultimately, that modified.
Ace Professional, as an example, began sending a request to the area relaxation.apizza[.]internet, which might then reply with content material from acedealex[.]xyz, which might ship the faux buying and selling interface. MBN_BitScan reached out to a server hosted by Amazon, which in flip beckoned flyerbit8[.]com, a website designed to seem like the professional Bitcoin service bitFlyer.
The method appeared one thing like this:
The faux interface gave the looks of permitting customers to deposit and withdraw cash and discipline customer support requests in actual time. To get the victims began, the scammers instructed them to switch cash into the Binance trade and, from there, from Binance to the faux app.
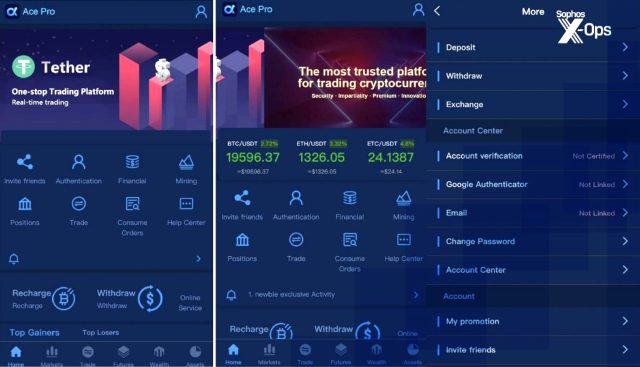
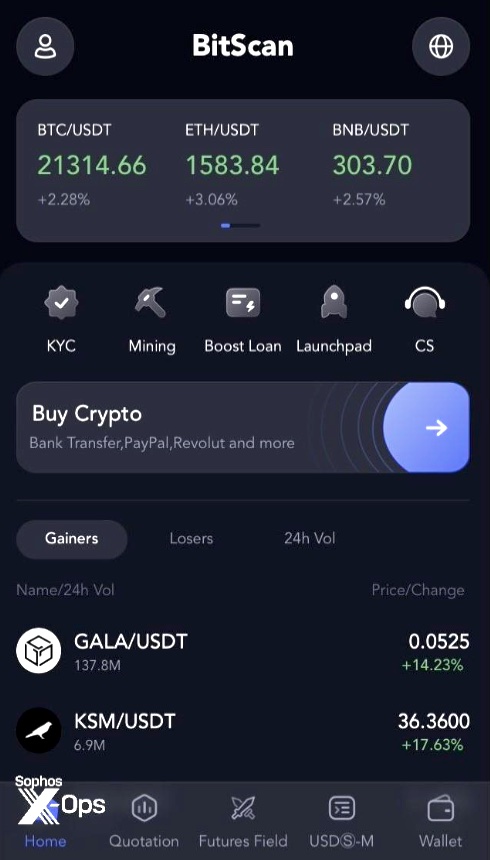
Faux buying and selling interface offered by MBM_BitScan.
[ad_2]
Source link








