[ad_1]
Getty Pictures
A federal Cyber Security Assessment Board has issued its report on what led to final summer time’s seize of a whole bunch of 1000’s of emails by Chinese language hackers from cloud prospects, together with federal businesses. It cites “a cascade of safety failures at Microsoft” and finds that “Microsoft’s safety tradition was insufficient” and desires to regulate to a “new regular” of cloud supplier concentrating on.
The report, mandated by President Biden within the wake of the far-reaching intrusion, particulars the steps that Microsoft took earlier than, throughout, and after the breach and in every case finds vital failure. The breach was “preventable,” regardless that it cites Microsoft as not understanding exactly how Storm-0558, a “hacking group assessed to be affiliated with the Folks’s Republic of China,” obtained in.
“All through this evaluate, the board recognized a sequence of Microsoft operational and strategic choices that collectively factors to a company tradition that deprioritized each enterprise safety investments and rigorous threat administration,” the report reads.
The report notes that Microsoft “absolutely cooperated with the Board’s evaluate.” A Microsoft spokesperson issued an announcement relating to the report. “We respect the work of the CSRB to analyze the affect of well-resourced nation state menace actors who function repeatedly and with out significant deterrence,” the assertion reads. “As we introduced in our Secure Future Initiative, latest occasions have demonstrated a must undertake a brand new tradition of engineering safety in our personal networks.” Together with hardening its programs and implementing extra sensors and logs to “detect and repel the cyber-armies of our adversaries,” Microsoft stated it might “evaluate the ultimate report for added suggestions.”
“Inaccurate public statements” and unsolved mysteries
The Cyber Security Assessment Board (CSRB), shaped two years in the past, consists of presidency and trade officers, from entities together with the Departments of Homeland Safety, Justice, and Protection, the NSA, FBI, and others. Microsoft gives cloud-based providers, together with Alternate and Azure, to quite a few authorities businesses, together with consulates.
Microsoft has beforehand provided a model of the intrusion story, one which notably avoids the phrases “vulnerability,” “exploit,” or “zero-day.” A Microsoft post in July 2023 cited an inactive signing key acquired by Storm-0558, which was then used to forge tokens for the Azure AD cloud service that shops keys for logins. This was “made potential by a validation error in Microsoft code,” Microsoft wrote.
Congress and authorities businesses called on Microsoft to offer far more disclosure, and others, together with Tenable’s CEO, offered even harsher assessments. In September, the corporate met them partway. It was an engineer’s account that was hacked, Microsoft claimed, giving attackers entry to a supposedly locked-down workstation, the patron signing key, and, crucially, entry to crash dumps moved right into a debugging atmosphere. A “race situation” prevented a mechanism that strips out signing keys and different delicate knowledge from crash dumps from functioning. Moreover, “human errors” allowed for an expired signing key for use in forging tokens for contemporary enterprise choices.
These sorts of unrevealing, withholding public statements have been cited by the CSRB in its discovering of Microsoft’s failures. The report cites “Microsoft’s choice to not appropriate, in a well timed method, its inaccurate public statements about this incident, together with a company assertion that Microsoft believed it had decided the probably root reason for the intrusion when actually, it nonetheless has not.” It additionally notes that Microsoft didn’t replace its September 2023 weblog submit in regards to the invasion trigger till March 2024, “because the Board was concluding its evaluate and solely after the Board’s repeated questioning about Microsoft’s plans to concern a correction.” (The up to date weblog submit notes that Microsoft has “not discovered a crash dump containing the impacted key materials.”)
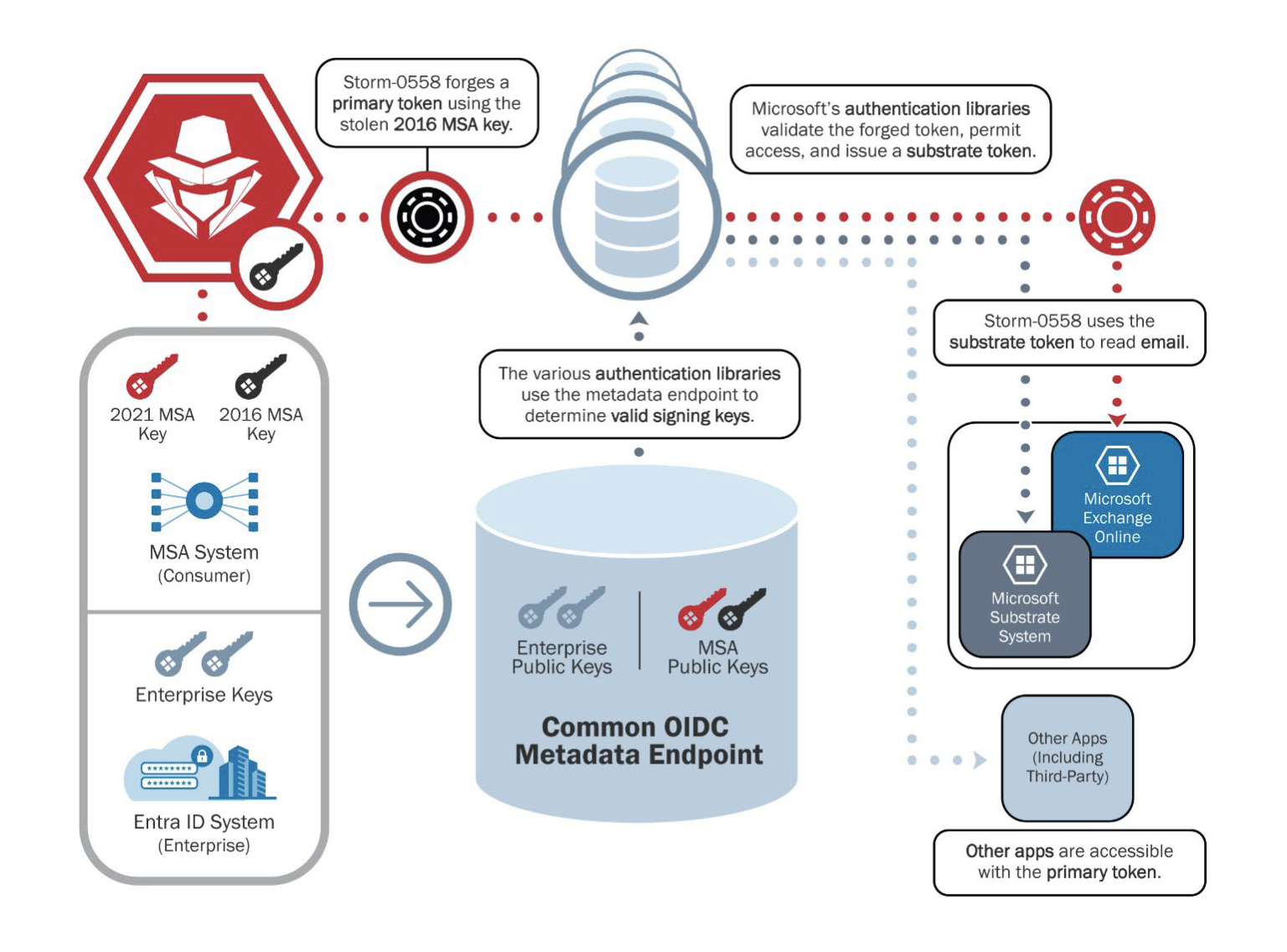
CSRB diagram detailing how Microsoft’s 2023 Alternate breach was perpetrated.
CSRB
[ad_2]
Source link








