[ad_1]
Aurich Lawson | Getty Photos
AI assistants have been extensively accessible for just a little greater than a 12 months, they usually have already got entry to our most non-public ideas and enterprise secrets and techniques. Individuals ask them about changing into pregnant or terminating or stopping being pregnant, seek the advice of them when contemplating a divorce, search details about drug habit, or ask for edits in emails containing proprietary commerce secrets and techniques. The suppliers of those AI-powered chat providers are keenly conscious of the sensitivity of those discussions and take energetic steps—primarily within the type of encrypting them—to forestall potential snoops from studying different folks’s interactions.
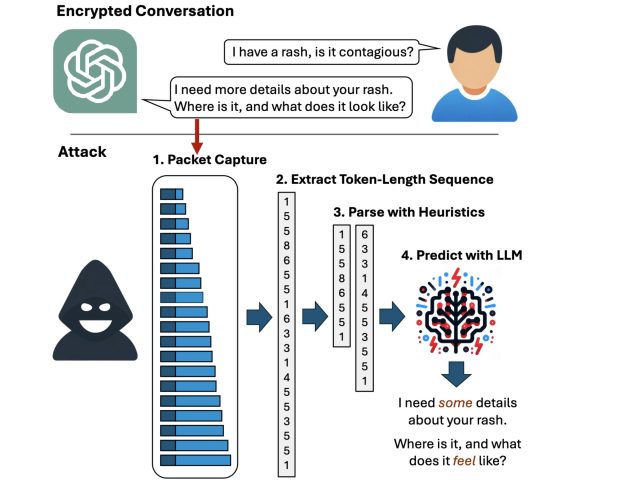
However now, researchers have devised an assault that deciphers AI assistant responses with shocking accuracy. The method exploits a side channel current in all the main AI assistants, aside from Google Gemini. It then refines the pretty uncooked outcomes by giant language fashions specifically skilled for the duty. The consequence: Somebody with a passive adversary-in-the-middle place—which means an adversary who can monitor the information packets passing between an AI assistant and the consumer—can infer the particular matter of 55 % of all captured responses, often with excessive phrase accuracy. The assault can deduce responses with excellent phrase accuracy 29 % of the time.
Token privateness
“At the moment, anyone can learn non-public chats despatched from ChatGPT and different providers,” Yisroel Mirsky, head of the Offensive AI Research Lab at Ben-Gurion College in Israel, wrote in an e mail. “This contains malicious actors on the identical Wi-Fi or LAN as a shopper (e.g., identical espresso store), or perhaps a malicious actor on the Web—anybody who can observe the visitors. The assault is passive and might occur with out OpenAI or their shopper’s information. OpenAI encrypts their visitors to forestall these sorts of eavesdropping assaults, however our analysis exhibits that the best way OpenAI is utilizing encryption is flawed, and thus the content material of the messages are uncovered.”
Mirsky was referring to OpenAI, however aside from Google Gemini, all different main chatbots are additionally affected. For instance, the assault can infer the encrypted ChatGPT response:
- Sure, there are a number of necessary authorized issues that {couples} ought to concentrate on when contemplating a divorce, …
as:
- Sure, there are a number of potential authorized issues that somebody ought to concentrate on when contemplating a divorce. …
and the Microsoft Copilot encrypted response:
- Listed below are a few of the newest analysis findings on efficient instructing strategies for college kids with studying disabilities: …
is inferred as:
- Listed below are a few of the newest analysis findings on cognitive habits remedy for youngsters with studying disabilities: …
Whereas the underlined phrases reveal that the exact wording isn’t excellent, the which means of the inferred sentence is extremely correct.
Weiss et al.
The next video demonstrates the assault in motion in opposition to Microsoft Copilot:
Token-length sequence side-channel assault on Bing.
A aspect channel is a way of acquiring secret info from a system by oblique or unintended sources, resembling bodily manifestations or behavioral traits, resembling the ability consumed, the time required, or the sound, gentle, or electromagnetic radiation produced throughout a given operation. By rigorously monitoring these sources, attackers can assemble sufficient info to recuperate encrypted keystrokes or encryption keys from CPUs, browser cookies from HTTPS visitors, or secrets from smartcards, The aspect channel used on this newest assault resides in tokens that AI assistants use when responding to a consumer question.
Tokens are akin to phrases which can be encoded to allow them to be understood by LLMs. To boost the consumer expertise, most AI assistants ship tokens on the fly, as quickly as they’re generated, in order that finish customers obtain the responses constantly, phrase by phrase, as they’re generated fairly than unexpectedly a lot later, as soon as the assistant has generated your complete reply. Whereas the token supply is encrypted, the real-time, token-by-token transmission exposes a beforehand unknown aspect channel, which the researchers name the “token-length sequence.”
[ad_2]
Source link








