[ad_1]
Getty Photos
Lots of of Microsoft Azure accounts, some belonging to senior executives, are being focused by unknown attackers in an ongoing marketing campaign that is aiming to steal delicate information and monetary property from dozens of organizations, researchers with safety agency Proofpoint mentioned Monday.
The marketing campaign makes an attempt to compromise focused Azure environments by sending account homeowners emails that combine strategies for credential phishing and account takeovers. The risk actors are doing so by combining individualized phishing lures with shared paperwork. A number of the paperwork embed hyperlinks that, when clicked, redirect customers to a phishing webpage. The large breadth of roles focused signifies the risk actors’ technique of compromising accounts with entry to numerous sources and tasks throughout affected organizations.
“Risk actors seemingly direct their focus towards a variety of people holding numerous titles throughout completely different organizations, impacting a whole bunch of customers globally,” a Proofpoint advisory said. “The affected consumer base encompasses a large spectrum of positions, with frequent targets together with Gross sales Administrators, Account Managers, and Finance Managers. People holding govt positions akin to “Vice President, Operations,” “Chief Monetary Officer & Treasurer,” and “President & CEO” had been additionally amongst these focused.”
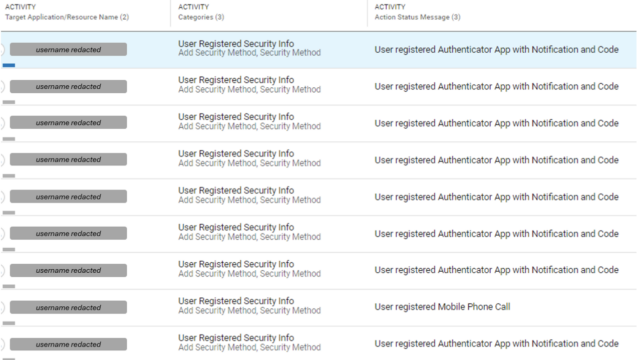
As soon as accounts are compromised, the risk actors safe them by enrolling them in varied types of multifactor authentication. This will make it tougher for victims to vary passwords or entry dashboards to look at latest logins. In some instances, the MFA used depends on one-time passwords despatched by textual content messages or telephone calls. In most cases, nonetheless, the attackers make use of an authenticator app with notifications and code.
Proofpoint
Proofpoint noticed different post-compromise actions together with:
- Information exfiltration. Attackers entry and obtain delicate recordsdata, together with monetary property, inner safety protocols, and consumer credentials.
- Inside and exterior phishing. Mailbox entry is leveraged to conduct lateral motion inside impacted organizations and to focus on particular consumer accounts with customized phishing threats.
- Monetary fraud. In an effort to perpetrate monetary fraud, inner e-mail messages are dispatched to focus on Human Assets and Monetary departments inside affected organizations.
- Mailbox guidelines. Attackers create devoted obfuscation guidelines supposed to cowl their tracks and erase all proof of malicious exercise from victims’ mailboxes.

Proofpoint
The compromises are coming from a number of proxies that act as intermediaries between the attackers’ originating infrastructure and the accounts being focused. The proxies assist the attackers align the geographical location assigned to the connecting IP deal with with the area of the goal. This helps to bypass varied geofencing insurance policies that prohibit the quantity and site of IP addresses that may entry the focused system. The proxy providers usually change mid-campaign, a technique that makes it tougher for these defending in opposition to the assaults to dam the IPs the place the malicious actions originate.
Different strategies designed to obfuscate the attackers’ operational infrastructure embody information internet hosting providers and compromised domains.
“Past using proxy providers, we now have seen attackers make the most of sure native fixed-line ISPs, doubtlessly exposing their geographical areas,” Monday’s submit said. “Notable amongst these non-proxy sources are the Russia-based ‘Selena Telecom LLC’, and Nigerian suppliers ‘Airtel Networks Restricted’ and ‘MTN Nigeria Communication Restricted.’ Whereas Proofpoint has not at present attributed this marketing campaign to any identified risk actor, there’s a risk that Russian and Nigerian attackers could also be concerned, drawing parallels to earlier cloud assaults.”
Find out how to test when you’re a goal
There are a number of telltale indicators of concentrating on. Essentially the most useful one is a selected consumer agent used throughout the entry part of the assault: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
Attackers predominantly make the most of this user-agent to entry the ‘OfficeHome’ sign-in software together with unauthorized entry to extra native Microsoft365 apps, akin to:
- Office365 Shell WCSS-Consumer (indicative of browser entry to Office365 purposes)
- Workplace 365 Alternate On-line (indicative of post-compromise mailbox abuse, information exfiltration, and e-mail threats proliferation)
- My Signins (utilized by attackers for MFA manipulation)
- My Apps
- My Profile
Proofpoint included the next Indicators of compromise:
| Indicator | Sort | Description |
| Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 | Person Agent | Person Agent concerned in assault’s entry part |
| Mozilla/5.0 (Home windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 | Person Agent | Person Agent concerned in assault’s entry and post-access phases |
| Mozilla/5.0 (Home windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 | Person Agent | Person Agent concerned in assault’s entry and post-access phases |
| sachacel[.]ru | Area | Area used for focused phishing threats |
| lobnya[.]com | Area | Supply area used as malicious infrastructure |
| makeapp[.]in the present day | Area | Supply area used as malicious infrastructure |
| alexhost[.]com | Area | Supply area used as malicious infrastructure |
| mol[.]ru | Area | Supply area used as malicious infrastructure |
| smartape[.]internet | Area | Supply area used as malicious infrastructure |
| airtel[.]com | Area | Supply area used as malicious infrastructure |
| mtnonline[.]com | Area | Supply area used as malicious infrastructure |
| acedatacenter[.]com | Area | Supply area used as malicious infrastructure |
| Sokolov Dmitry Nikolaevich | ISP | Supply ISP used as malicious infrastructure |
| Dom Tehniki Ltd | ISP | Supply ISP used as malicious infrastructure |
| Selena Telecom LLC | ISP | Supply ISP used as malicious infrastructure |
Because the marketing campaign is ongoing, Proofpoint could replace the indications as extra grow to be accessible. The corporate suggested firms to pay shut consideration to the consumer agent and supply domains of incoming connections to worker accounts. Different useful defenses are using safety defenses that search for indicators of each preliminary account compromise and post-compromise actions, figuring out preliminary vectors of compromise akin to phishing, malware, or impersonation, and setting up auto-remediation insurance policies to drive out attackers rapidly within the occasion they get in.
[ad_2]
Source link








