[ad_1]
Aurich Lawson | Getty Pictures
A current transfer by Google to populate the Web with eight new top-level domains is prompting issues that two of the additions might be a boon to on-line scammers who trick individuals into clicking on malicious hyperlinks.
Regularly abbreviated as TLD, a top-level area is the rightmost section of a site title. Within the early days of the Web, they helped classify the aim, geographic area, or operator of a given area. The .com TLD, as an illustration, corresponded to websites run by industrial entities, .org was used for nonprofit organizations, .web for Web or community entities, .edu for faculties and universities, and so forth. There are additionally nation codes, equivalent to .uk for the UK, .ng for Nigeria, and .fj for Fiji. One of many earliest Web communities, The WELL, was reachable at www.nicely.sf.ca.us.
Since then, the organizations governing Web domains have rolled out hundreds of recent TLDs. Two weeks in the past, Google added eight new TLDs to the Web, bringing the entire variety of TLDs to 1,480, according to the Web Assigned Numbers Authority, the governing physique that oversees the DNS Root, IP addressing, and different Web protocol assets.
Two of Google’s new TLDs—.zip and .mov—have sparked scorn in some safety circles. Whereas Google entrepreneurs say the purpose is to designate “tying issues collectively or transferring actually quick” and “transferring photos and no matter strikes you,” respectively, these suffixes are already broadly used to designate one thing altogether totally different. Particularly, .zip is an extension utilized in archive information that use a compression format often known as zip. The format .mov, in the meantime, seems on the finish of video information, often after they had been created in Apple’s QuickTime format.
Many safety practitioners are warning that these two TLDs will trigger confusion after they’re displayed in emails, on social media, and elsewhere. The reason being that many websites and software program mechanically convert strings like “arstechnica.com” or “mastodon.social” right into a URL that, when clicked, leads a person to the corresponding area. The fear is that emails and social media posts that discuss with a file equivalent to setup.zip or trip.mov will mechanically flip them into clickable hyperlinks—and that scammers will seize on the anomaly.
“Risk actors can simply register domains which are probably for use by different individuals to casually discuss with file names,” Randy Pargman, director of risk detection at safety agency Proofpoint, wrote in an e mail. “They’ll then use these conversations that the risk actor didn’t even need to provoke (or take part in) to lure individuals into clicking and downloading malicious content material.”
Undoing years of anti-phishing and anti-deception consciousness
A scammer with management of the area pictures.zip, as an illustration, might exploit the decades-long behavior of individuals archiving a set of pictures inside a zipper file after which sharing them in an e mail or on social media. Moderately than rendering pictures.zip as plaintext, which might have occurred earlier than Google’s transfer, many websites and apps at the moment are changing them to a clickable area. A person who thinks they’re accessing a photograph archive from somebody they know might as a substitute be taken to a web site created by scammers.
Scammers “might simply set it as much as ship a zipper file obtain each time anybody visits the web page and embrace any content material they need within the zip file, equivalent to malware,” stated Pargman.
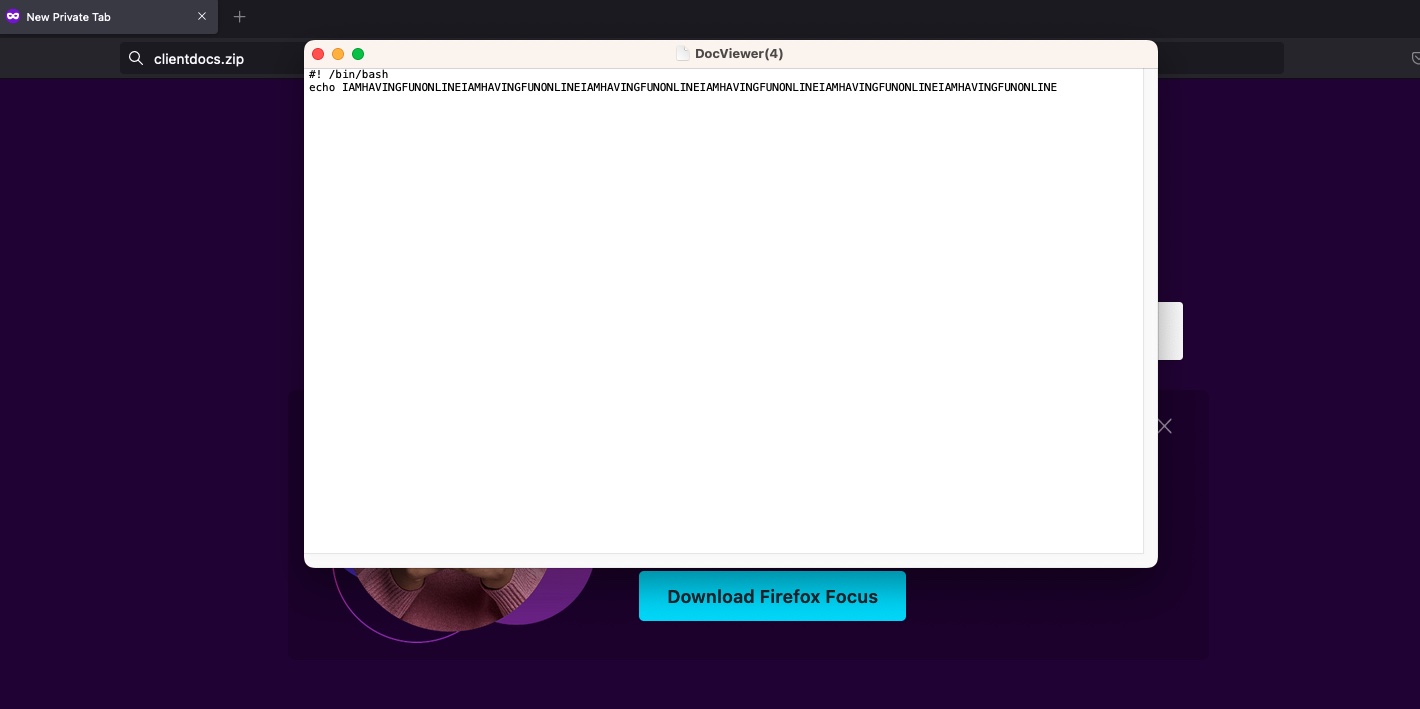
A number of newly created websites show what this sleight of hand would possibly appear to be. Amongst them are setup.zip and steaminstaller.zip, which use domains that generally discuss with naming conventions for installer information. Particularly poignant is clientdocs.zip, a website that mechanically downloads a bash script that reads:
#! /bin/bash echo IAMHAVINGFUNONLINEIAMHAVINGFUNONLINEIAMHAVINGFUNONLINEIAMHAVINGFUNONLINEIAMHAVINGFUNONLINEIAMHAVINGFUNONLINE
It’s not laborious to check risk actors utilizing this system in ways in which aren’t practically as comical.
“The benefit for the risk actor is that they didn’t even need to ship the messages to entice potential victims to click on on the hyperlink—they simply needed to register the area, arrange the web site to serve malicious content material, and passively look forward to individuals to by accident create hyperlinks to their content material,” Pargman wrote. “The hyperlinks appear far more reliable as a result of they arrive within the context of messages or posts from a trusted sender.”
[ad_2]
Source link








