[ad_1]
Aurich Lawson | Getty Photos
By now, you’ve most likely heard a couple of new AI-based password cracker that may compromise your password in seconds through the use of synthetic intelligence as an alternative of extra conventional strategies. Some retailers have referred to as it “terrifying,” “worrying,” “alarming,” and “savvy.” Different publications have fallen over themselves to report that the software can crack any password with as much as seven characters—even when it has symbols and numbers—in below six minutes.
As with so many issues involving AI, the claims are served with a beneficiant portion of smoke and mirrors. PassGAN, because the software is dubbed, performs no higher than extra typical cracking strategies. Briefly, something PassGAN can do, these extra tried and true instruments do as nicely or higher. And like so most of the non-AI password checkers Ars has criticized up to now—e.g., here, here, and here—the researchers behind PassGAN draw password recommendation from their experiment that undermines actual safety.
Instructing a machine to crack
PassGAN is a shortened mixture of the phrases “Password” and “generative adversarial networks.” PassGAN is an strategy that debuted in 2017. It makes use of machine studying algorithms operating on a neural community instead of typical strategies devised by people. These GANs generate password guesses after autonomously studying the distribution of passwords by processing the spoils of earlier real-world breaches. These guesses are utilized in offline assaults made attainable when a database of password hashes leaks on account of a safety breach.
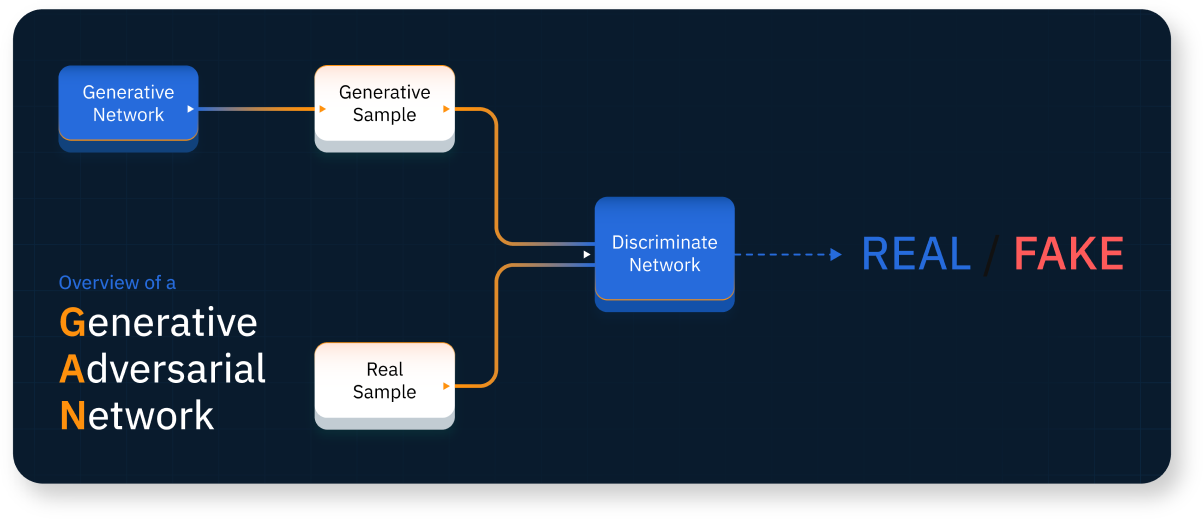
An outline of a generative adversarial community.
Conventional password guessing makes use of lists of phrases numbering within the billions taken from earlier breaches. In style password-cracking purposes like Hashcat and John the Ripper then apply “mangling guidelines” to those lists to allow variations on the fly.
When a phrase akin to “password” seems in a glossary, as an example, the mangling guidelines rework it into variations like “Password” or “p@ssw0rd” despite the fact that they by no means seem instantly within the glossary. Examples of real-world passwords cracked utilizing mangling embody: “Coneyisland9/,” “momof3g8kids,” “Oscar+emmy2″ “k1araj0hns0n,” “Sh1a-labe0uf,” “Apr!l221973,” “Qbesancon321,” “DG091101%,” “@Yourmom69,” “ilovetofunot,” “windermere2313,” “tmdmmj17,” and “BandGeek2014.” Whereas these passwords could look like sufficiently lengthy and sophisticated, mangling guidelines make them extraordinarily straightforward to guess.
These guidelines and lists run on clusters focusing on parallel computing, that means they will carry out repetitive duties like cranking out massive numbers of password guesses a lot sooner than CPUs can. When poorly suited algorithms are used, these cracking rigs can rework a plaintext phrase akin to “password” right into a hash like “5baa61e4c9b93f3f0682250b6cf8331b7ee68fd8” billions of instances every second.
One other approach that makes phrase lists far more highly effective is called a combinator attack. As its identify suggests, this assault combines two or extra phrases within the listing. In a 2013 exercise, password-cracking professional Jens Steube was capable of recuperate the password “momof3g8kids” as a result of he already had “momof3g” and “8kids” in his lists.
Password cracking additionally depends on a method referred to as brute drive, which, regardless of its misuse as a generic time period for cracking, is distinctly completely different from cracks that use phrases from an inventory. Moderately, brute drive cracking tries each attainable mixture for a password of a given size. For a password as much as six characters, it begins by guessing “a” and runs by each attainable string till it reaches “//////.”
The variety of attainable mixtures for passwords of six or fewer characters is sufficiently small to finish in seconds for the sorts of weaker hashing algorithms the Dwelling Safety Heroes appear to ascertain in its PassGAN writeup.
[ad_2]
Source link








