[ad_1]
Getty Photographs
Broadly considered one of many Web’s top threats, the Emotet botnet has returned after a months-long hiatus—and it has some new methods.
Final week, Emotet appeared for the first time this yr after a four-month hiatus. It returned with its trademark exercise—a wave of malicious spam messages that seem to return from a recognized contact, handle the recipient by title, and appear to be replying to an current e mail thread. When Emotet has returned from earlier breaks, it introduced new methods designed to evade endpoint safety merchandise and to trick customers into clicking on hyperlinks or enabling harmful macros in connected Microsoft Workplace paperwork. Final week’s resumption of exercise was no totally different.
A malicious e mail despatched final Tuesday, as an example, connected a Phrase doc that had an enormous quantity of extraneous knowledge added to the tip. Because of this, the file was greater than 500MB in measurement, large enough to forestall some safety merchandise from with the ability to scan the contents. This method, generally known as binary padding or file pumping, works by including zeros to the tip of the doc. Within the occasion somebody is tricked into enabling the macro, the malicious Home windows DLL file that’s delivered can also be pumped, inflicting it to mushroom from 616kB to 548.1MB, researchers from safety agency Pattern Micro said on Monday.
One other evasion trick noticed within the connected doc: excerpts from the Herman Melville traditional novel Moby Dick, which seem in a white font over a white web page so the textual content isn’t readable. Some safety merchandise robotically flag Microsoft Workplace recordsdata containing only a macro and a picture. The invisible textual content is designed to evade such software program whereas not arousing the suspicion of the goal.
Deep Intuition
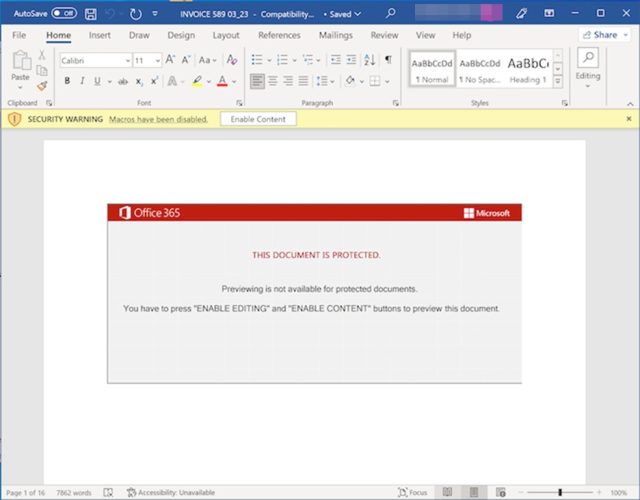
When opened, the Phrase paperwork current a graphic that claims the content material can’t be accessed except the consumer clicks the “allow content material” button. Final yr, Microsoft started disabling macros downloaded from the Web by default.
Pattern Micro
Clicking the “allow content material” button undoes that default and permits the macro to run. The macro causes Workplace to obtain a .zip file from a respectable web site that has been hacked. Workplace will then unzip the archive file and execute the inflated Emotet DLL that infects the system.
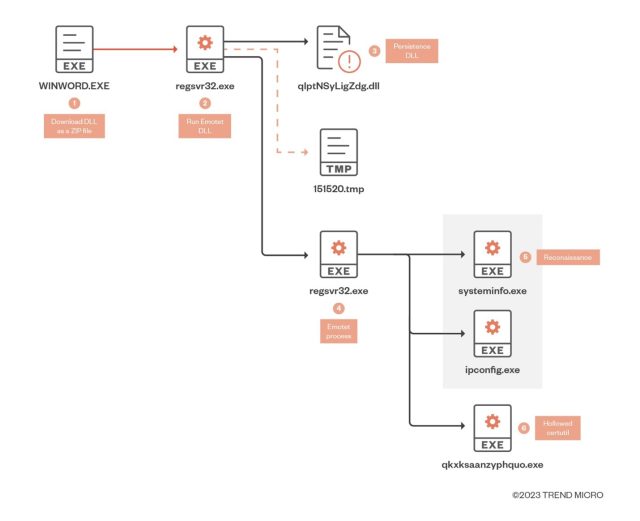
As soon as it has contaminated a sufferer’s system, the malware pilfers passwords and different delicate knowledge and makes use of the system to ship malicious spam to different customers. The malware may obtain further malware such because the Ryuk ransomware or the TrickBot malware. The an infection chain seems to be like this:
Pattern Micro
The eye to element seen on this newest revival is signature Emotet conduct. For years, the botnet has painstakingly copied obtained e mail conversations from contaminated machines and embedded them into malicious spam despatched to different events within the thread. By following up on an e mail from somebody the goal has communicated with previously, the malicious spam message stands a greater likelihood of going undetected. Emotet may gain access to Wi-Fi networks and infect related gadgets.
With the return of Emotet, individuals needs to be looking out for malicious emails, even when they seem to return from trusted sources, name the goal by title, and embody beforehand despatched and obtained emails. There’s hardly ever a very good cause for enabling macros in paperwork despatched by e mail. Folks ought to refuse to permit them to run with out first speaking with the sender by cellphone, prompt message, or one other non-email medium.
Nations hit the toughest within the newest Emotet run are European, Asian Pacific, and Latin American.
[ad_2]
Source link








