[ad_1]
Malware that exploits unpatched vulnerabilities in 30 completely different WordPress plugins has contaminated a whole lot if not hundreds of websites and should have been in energetic use for years, in accordance with a writeup revealed final week.
The Linux-based malware installs a backdoor that causes contaminated websites to redirect guests to malicious websites, researchers from safety agency Dr.Net said. It’s additionally in a position to disable occasion logging, go into standby mode, and shut itself down. It will get put in by exploiting already-patched vulnerabilities in plugins that web site homeowners use so as to add performance like reside chat or metrics-reporting to the core WordPress content material administration system.
“If websites use outdated variations of such add-ons, missing essential fixes, the focused net pages are injected with malicious JavaScripts,” Dr.Net researchers wrote. “In consequence, when customers click on on any space of an attacked web page, they’re redirected to different websites.”
Searches corresponding to this one point out that greater than 1,300 websites comprise the JavaScript that powers the backdoor. It’s doable that a few of these websites have eliminated the malicious code because the final scan. Nonetheless, it offers a sign of the attain of the malware.
The plugins exploited embrace:
- WP Reside Chat Assist Plugin
- WordPress – Yuzo Associated Posts
- Yellow Pencil Visible Theme Customizer Plugin
- Easysmtp
- WP GDPR Compliance Plugin
- Newspaper Theme on WordPress Entry Management (vulnerability CVE-2016-10972)
- Thim Core
- Google Code Inserter
- Complete Donations Plugin
- Submit Customized Templates Lite
- WP Fast Reserving Supervisor
- Fb Reside Chat by Zotabox
- Weblog Designer WordPress Plugin
- WordPress Final FAQ (vulnerabilities CVE-2019-17232 and CVE-2019-17233)
- WP-Matomo Integration (WP-Piwik)
- WordPress ND Shortcodes For Visible Composer
- WP Reside Chat
- Coming Quickly Web page and Upkeep Mode
- Hybrid
- Brizy WordPress Plugin
- FV Flowplayer Video Participant
- WooCommerce
- WordPress Coming Quickly Web page
- WordPress theme OneTone
- Easy Fields WordPress Plugin
- WordPress Delucks web optimization plugin
- Ballot, Survey, Kind & Quiz Maker by OpinionStage
- Social Metrics Tracker
- WPeMatico RSS Feed Fetcher
- Wealthy Critiques plugin
“If a number of vulnerabilities are efficiently exploited, the focused web page is injected with a malicious JavaScript that’s downloaded from a distant server,” the Dr.Net writeup defined. “With that, the injection is completed in such a method that when the contaminated web page is loaded, this JavaScript might be initiated first—whatever the unique contents of the web page. At this level, at any time when customers click on anyplace on the contaminated web page, they are going to be transferred to the web site the attackers want customers to go to.”
The JavaScript incorporates hyperlinks to quite a lot of malicious domains, together with:
lobbydesires[.]com
letsmakeparty3[.]ga
deliverygoodstrategies[.]com
gabriellalovecats[.]com
css[.]digestcolect[.]com
clon[.]collectfasttracks[.]com
Depend[.]trackstatisticsss[.]com
The screenshot under reveals how the JavaScript seems within the web page supply of the contaminated website:
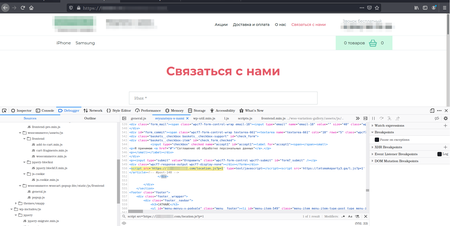
Dr.Net
The researchers discovered two variations of the backdoor: Linux.BackDoor.WordPressExploit.1 and Linux.BackDoor.WordPressExploit.2. They stated the malware might have been in use for 3 years.
WordPress plugins have lengthy been a standard means for infecting websites. Whereas the safety of the principle utility is pretty sturdy, many plugins are riddled with vulnerabilities that may result in an infection. Criminals use contaminated websites to redirect guests to websites used for phishing, advert fraud, and distributing malware.
Folks operating WordPress websites ought to be sure that they’re utilizing essentially the most present variations of the principle software program in addition to any plugins. They need to prioritize updating any of the plugins listed above.
[ad_2]
Source link








