[ad_1]
Aurich Lawson | Getty Pictures
Microsoft’s Edge browser has changed Web Explorer in nearly each regard, however some exceptions stay. A type of, deep inside Microsoft Phrase, was exploited by a North-Korean-backed group this fall, Google safety researchers declare.
It is not the first time the government-backed APT37 has utilized Web Explorer’s lingering presence, as Google’s Risk Evaluation Group (TAG) notes in a blog post. APT37 has had repeated success focusing on South Korean journalists and activists, plus North Korean defectors, by means of a restricted however nonetheless profitable Web Explorer pathway.
The final exploit focused these heading to Daily NK, a South Korean web site devoted to North Korean information. This one concerned the Halloween crowd crush in Itaewon, which killed at the least 151 folks. A Microsoft Phrase .docx doc, named as if it have been timed and dated lower than two days after the incident and labeled “accident response state of affairs,” began circulating. South Korean customers started submitting the document to the Google-owned VirusTotal, the place it was flagged with CVE-2017-0199, a long-known vulnerability in Phrase and WordPad.
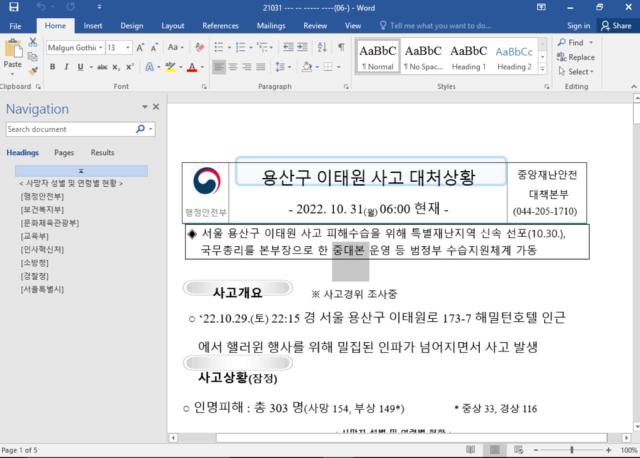
Simply as in April 2017, the doc, for those who click on to permit Phrase/WordPad to view it outdoors the no-download “Protected View,” downloads a wealthy textual content template from an attacker-controlled server, then grabs extra HTML that appears like Wealthy Textual content Format templates. Workplace and WordPad intrinsically use Web Explorer to render HTML in what Microsoft describes as “specifically crafted information,” giving attackers a technique to then herald varied malware payloads. Whereas patched that same month, the vulnerability continued; it was one of many vectors exploited in a Petya wave more than a year later.
The precise vulnerability has to do with Web Explorer’s JavaScript engine. An error throughout just-in-time optimization results in a data type confusion and memory writing. This explicit exploit additionally cleaned up after itself, clearing the Web Explorer cache and historical past of its presence. Whereas Google’s TAG does not know what payloads have been delivered, APT37 has beforehand circulated exploits that triggered BLUELIGHT, ROKRAT, and DOLPHIN, all specializing in North Korean political and financial pursuits. (North Korean hackers aren’t averse to a Chrome exploit, although.)
Microsoft patched the specific exploit in its JScript engine, however this being the fifth 12 months of remote-code Phrase doc assaults, it looks like they will be round for some time longer. And North Korean actors shall be desirous to act on them.
[ad_2]
Source link








