[ad_1]
Getty Pictures
Wednesday’s scheduled launch by NASA of the Artemis I mission would be the first built-in check of the company’s SLS rocket and Orion spacecraft, which have been in growth for 16 years and are anticipated to usher in a brand new period of area exploration. The uncrewed mission may also be solely the second time a community customary referred to as time-triggered Ethernet has been taken into area, with the primary being Orion’s orbital test flight in 2014.
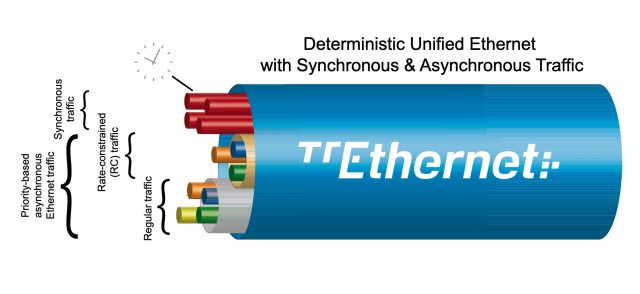
Time-triggered Ethernet (TTE) is an instance of a mixed-criticality community, which is able to routing visitors with differing ranges of timing and completely different fault tolerance necessities over the identical set of {hardware}. Till now, spacecraft typically relied on one community to transmit safety-critical or mission-critical messages and a number of fully segregated ones for carrying video conferencing and different kinds of less-critical visitors.
TTTech
Engineers constructed a greater mousetrap. The mice defeat it anyway
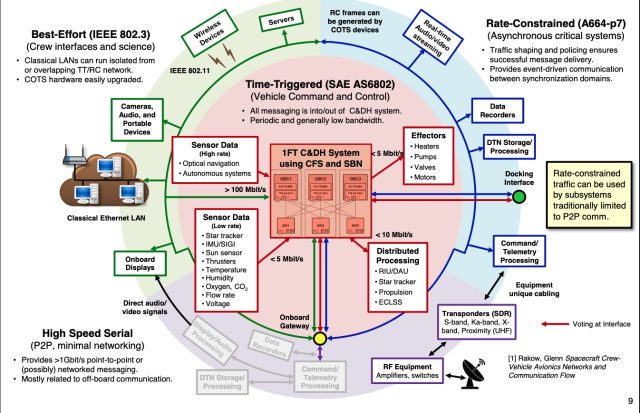
Orion is the primary spacecraft to depend on a TTE community to route mixed-criticality visitors, whether or not, NASA says, it is for very important techniques like navigation and life assist, file transfers which can be important for supply however not timing, or non-critical duties reminiscent of crew videoconferencing. TTE—which may also be utilized in NASA’s Lunar Gateway area station and the ESA’s Ariane 6 launcher—is essential for decreasing the dimensions, weight, price, and energy necessities of contemporary spacecraft.
NASA
Security-critical techniques, like these for steering and engine management, typically work solely when community messages are despatched and obtained at intervals as small as 40 to 50 milliseconds. Delayed or dropped messages could be catastrophic. The opposite finish of the criticality spectrum incorporates messages despatched by scientific devices, which regularly come within the type of industrial off-the-shelf units and are supplied by universities or exterior researchers with minimal security evaluation from NASA. Whereas it’s 100% suitable with the Ethernet customary, TTE can also be capable of ship messages that engineers usually reserve for special-purpose networks.
To stop less-important messages from interfering with important ones, TTE gives two key advantages not out there in common Ethernet. They’re:
- A time-triggered paradigm the place all units are tightly synchronized and ship messages at a predetermined schedule. This will cut back latency to a whole lot of microseconds and jitter to close zero.
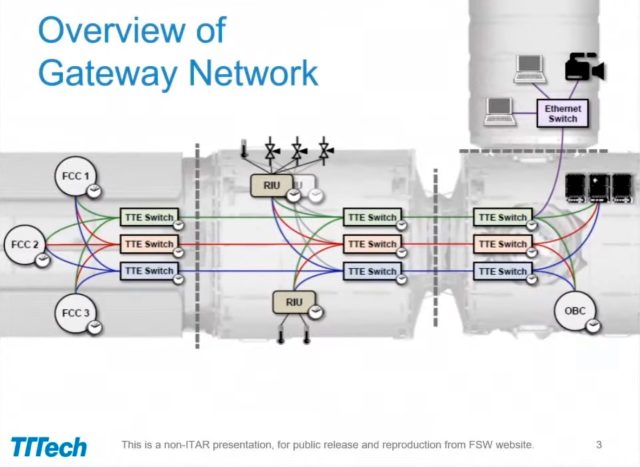
- Fault tolerance—TTE replicates the entire community into a number of planes and forwards messages throughout all planes directly. The TTE community onboard Gateway has three planes.
TTTech
On Tuesday, researchers published findings that, for the primary time, break TTE’s isolation ensures. The result’s PCspooF, an assault that permits a single non-critical system related to a single airplane to disrupt synchronization and communication between TTE units on all planes. The assault works by exploiting a vulnerability within the TTE protocol. The work was accomplished by researchers on the College of Michigan, the College of Pennsylvania, and NASA’s Johnson House Middle.
“Our analysis reveals that profitable assaults are potential in seconds and that every profitable assault could cause TTE units to lose synchronization for as much as a second and drop tens of TT messages—each of which can lead to the failure of important techniques like plane or cars,” the researchers wrote. “We additionally present that, in a simulated spaceflight mission, PCspooF causes uncontrolled maneuvers that threaten security and mission success.”

NASA
PCspooF could be constructed onto as little as a 2.5 cm×2.5 cm space of a single-layer printed circuit board and requires minimal energy and community bandwidth, which permits a malicious system to mix in with all the opposite best-effort units related to the community. The researchers privately reported their findings to NASA and different massive stakeholders in TTE. In an e mail, a NASA consultant wrote, “NASA groups are conscious of the findings from analysis on TTE and have taken proactive measures to make sure potential dangers to spacecraft are appropriately mitigated.”
[ad_2]
Source link








